BLOG

Cybercrime: Costly, imminent threat to the banking world
Patrick Gardner, Managing Partner at C8 Secure
Increased internet usage, online banking and digitalization in finance have made financial institutions vulnerable to cybercrime and cyber attacks.
The year 2022 saw several significant cyber incidents in the finance industry. On April 17, Beanstalk Farms, a decentralized finance platform, lost $180 million in a cryptocurrency heist. On April 11, the FakeCalls banking trojan was discovered, capable of talking to victims and impersonating bank employees. CashMama, an India-based loans app, reported a data breach on April 6. The breach exposed customer data that was collected and stored.
Lazarus was discovered to be using ‘Trojanized’ decentralized finance apps to deliver malware in a spearphishing campaign on April 1, 2022. While the largest bank in Russia, Sberbank and the Moscow Stock Exchange, both suffered DDoS attacks on February 28, 2022, resulting in their websites being shut down.
In 2022, data breaches in the United States cost an average of $9.44 million. The financial sector experienced a significant impact, with the cost of data breaches in this sector reaching $5.97 million globally.
Cyber attack data indicates financial phishing attacks represented 36.3 percent of total global attacks 2022. In the same year, investment fraud became the most costly form of cybercrime, resulting in an average loss of $70,811 per victim.
Types of cybercrime threats to banking industry
Cybercriminals often use various cybercrimes to bypass security and take advantage of vulnerabilities.
Phishing attacks and social engineering
Phishing attacks involve attackers posing as trustworthy entities, such as banks, online services or reputable organizations, to deceive people into sharing sensitive information.
These attacks usually take place through fraudulent emails, text messages or websites.
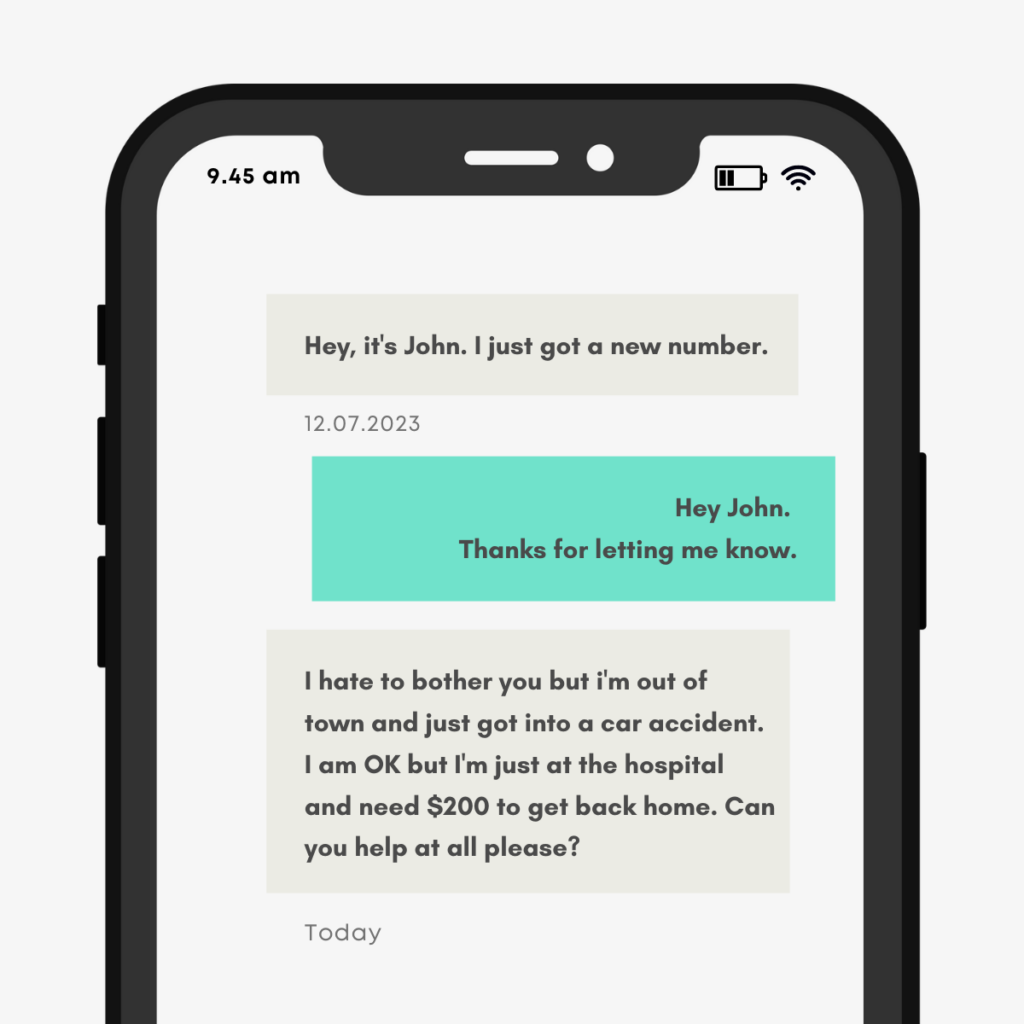 In a Business Email Compromise (BEC) scam, cybercriminals send fake emails that seem to originate from a trustworthy source, like the CEO or a reliable supplier. The emails are designed to imitate the organization’s communication style and contain convincing appeals for fund transfers, invoice payments or confidential data. The scammers may also alter the email header or use fake email addresses to make the emails seem authentic.
In a Business Email Compromise (BEC) scam, cybercriminals send fake emails that seem to originate from a trustworthy source, like the CEO or a reliable supplier. The emails are designed to imitate the organization’s communication style and contain convincing appeals for fund transfers, invoice payments or confidential data. The scammers may also alter the email header or use fake email addresses to make the emails seem authentic.
With the use of AI-powered chatbots on the rise, experts warn that it may also make it easier for fraudulent phishing emails to bypass fundamental defense mechanisms, such as spelling and grammatical error detection. It is because chatbots can generate more sophisticated and convincing messages that can fool users into thinking they are legitimate.
Cybercriminals use social engineering to persuade people to reveal sensitive information or perform actions that jeopardize security. Unlike technical hacking methods that exploit computer systems’ vulnerabilities, social engineering targets human psychology to exploit trust, authority or ignorance.
Social engineering tactics involve various techniques, such as pretexting (fabricating a scenario to extract information), baiting (leaving infected physical devices to lure victims) or tailgating (gaining physical access to restricted areas by following authorized people).
Malware and ransomware
Malicious software, also known as malware, poses a significant threat to banking systems and networks. Cybercriminals use various types of malware to exploit vulnerabilities in banking systems.
Banking Trojans are malware created to steal users’ banking credentials and other sensitive data. These Trojans work by intercepting login credentials or manipulating online banking transactions to redirect funds to the attacker’s account.
Distributed Denial of Service (DDoS) attacks are not considered traditional malware, but they involve flooding a banking system or network with an excessive amount of traffic, rendering it inaccessible to authorized users.
These attacks can disrupt online banking services. It causes inconvenience to customers and creates opportunities for cybercriminals to carry out other malicious activities.
For banking systems, ransomware attacks can freeze operations, block access to important data and interrupt financial transactions until the ransom is paid.
ATM and card skimming
ATM and card skimming is a prevalent cybercrime targeting banking customers using automated teller machines (ATMs) and payment card systems. Cybercriminals put skimming devices on ATMs or payment terminals to covertly record card data. These devices can be placed on the card slot or inside the ATM.
Besides skimming devices, criminals may also attach small cameras or overlays on ATM keypads to record customers’ PINs as they enter them.
By obtaining stolen card data and PINs, criminals can generate counterfeit cards or use the information for unauthorized transactions, such as cash withdrawals or fraudulent purchases.
Sophisticated cyber attack
Advanced Persistent Threats (APTs) are targeted and sophisticated cyber attacks that pose a significant danger to financial institutions.
Typically, well-resourced and skilled threat actors, such as state-sponsored groups or organized cybercriminal organizations, conduct APTs. These attacks are identified by their secretive nature, extended duration and continuous persistence in compromising a target’s systems and networks.
The SolarWinds Sunburst attack, detected in 2020 and had far-reaching consequences through 2021, is one of the most popular APTs in recent times. Another recent APT is Aquatic Panda, believed to be affiliated with China.
According to MITRE’s ATT&CK database, it has been active since at least May 2020. It gathered intelligence and conducted industrial espionage in the technology, telecom and government sectors.
Costly implications for financial institutions
Cybercriminals can make unauthorized transactions such as fund transfers, withdrawals or purchases once they can access someone’s bank account or payment card information. It can lead to direct monetary losses for the victim, with the stolen funds being removed from their account without their permission.
Law enforcement agencies or specialized cybersecurity firms are often hired to investigate cases of fraud or theft. Such investigations require time, resources and expertise to collect evidence, pursue suspects and construct a legal case. The expenses involved in investigations can accumulate, particularly in complex cases that span multiple jurisdictions.
Financial institutions may also have to take legal action to recoup losses, bring criminals to justice, or protect themselves from liability claims. It entails retaining legal representation, initiating lawsuits, attending legal proceedings and participating in settlement discussions.
Legal actions can be lengthy and costly, involving various fees, such as court, attorney and other related expenses.
A bank’s reputation is vital for attracting new customers and retaining existing ones. If news of fraudulent activities or data breaches becomes public, it can damage the bank’s reputation and create negative perceptions in the market.
Customers who have lost faith in a bank’s security may close their accounts and move their business to another institution. They may prefer to use alternative financial institutions that they consider superior security measures.
To combat the costly implications of cybercrime, financial institutions must adopt a comprehensive cybersecurity strategy that aligns with industry best practices. By partnering with C8 Secure, online businesses in the banking industry can have peace of mind knowing that a trusted security partner is safeguarding their infrastructure and data.
“We realized an immediate return on our investment and greatly enhanced our threat detection and remediation capabilities utilizing C8 Secure’s Managed Security Services,” said Roland V. Oscuro, CISO Philippines National Bank.
C8 Secure implements a comprehensive security strategy comprising many layers of protection. Designed with tomorrow’s needs in mind, C8 Secure protects from the edge through to the endpoint and cloud. This includes, managed SIEM/SOC, EDR and MDR, DDoS and Web Application Attack Protection (WAAP), ensuring the resilience of critical infrastructure.
Learn more about C8 Secure here.
RECENT POSTS
Securing a decentralized future: The importance of cybersecurity in Web3
7 Jun, 2023
The dawn of the decentralized web is upon us, and the rise of Web3 technology is a testament to this fact. Web3 is an alternative to today’s highly censored internet and is becoming increasingly popular, which calls for urgent measures to ensure that the foundation of this revolution remains secure and trustworthy.
DOWNLOAD BROCHURE
For more information, please download our solutions brochure